This post aims to add some sense to the whole Azure account, subscription, tenant, directory layout as well as Azure AD (Azure Active Directory) across both ASM (Classic) and ARM. I will discuss the different administrator roles from an ASM (Azure Service Management) perspective and then take a look at the new changed/updated administrator roles with ARM (Azure Resource Manager).
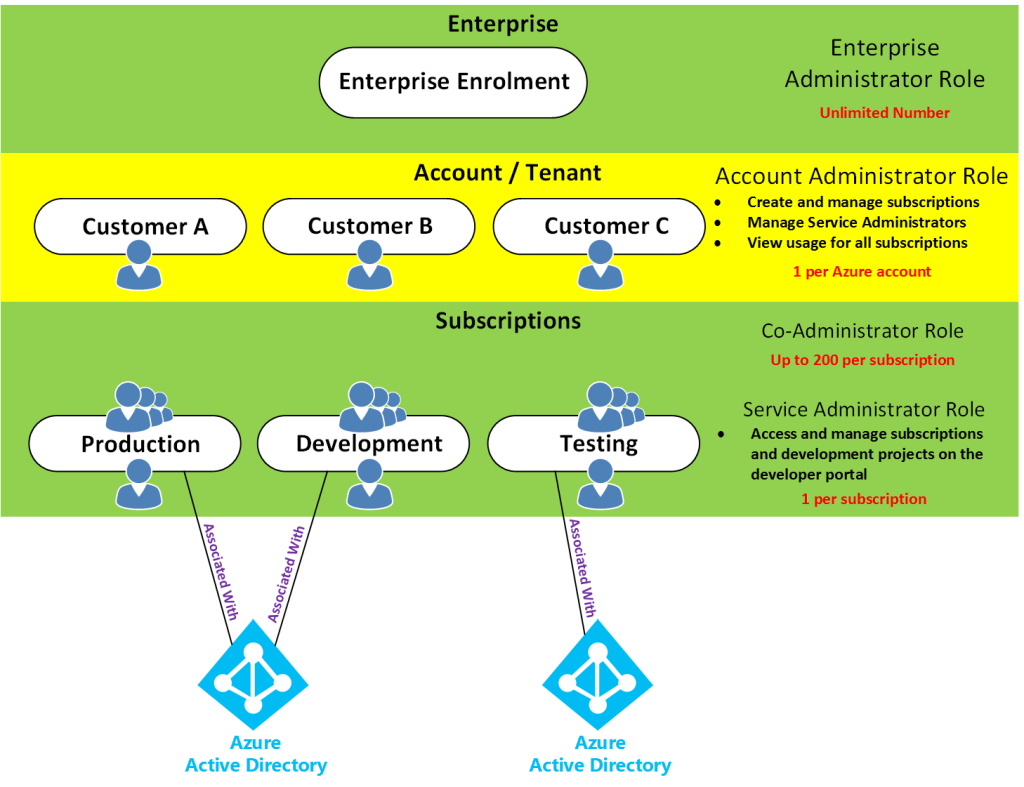
Access control in Azure starts from a billing perspective. The actual owner of an Azure account – accessed by visiting the Azure Accounts Center – is the Account Administrator (AA). Subscriptions are a container for billing, but they also act as a security boundary. No matter ASM or ARM, every Azure subscription has a trust relationship with at least one Azure AD instance. This means that a subscription trusts that directory to authenticate users, services, and devices. Multiple Azure subscriptions can trust the same directory, but a subscription trusts only one directory.
As for the directory, the directory that Azure uses is Azure AD. Azure AD is a separate service on its own which sits by itself and is used by all of Azure (ASM & ARM) and also Office 365. Even though there is one Azure AD, there are two subscription/authentication modes of Azure.
If you signed up to Azure using a Microsoft account, then you will get Azure with a Default Directory which you can see in the classic portal.
This Default Directory is just like normal Azure AD, however you can’t add anyone to any ASM/ARM Azure administrator role picked from this Default Directory itself, you can only add people to ASM/ARM Azure administrator roles using their Microsoft Accounts.
The opposite to this, if you signed up to Azure using the alternative methods then you can add people to ASM/ARM Azure administrator roles using both their Microsoft Accounts and/or Organisational Accounts. Until recently, you could only sign up for a new Microsoft Azure subscription using your Microsoft account (Windows Live ID). Azure now supports using either of the following two account methods to sign up: Microsoft Accounts or Work or school accounts, see https://azure.microsoft.com/en-us/documentation/articles/sign-up-organization/
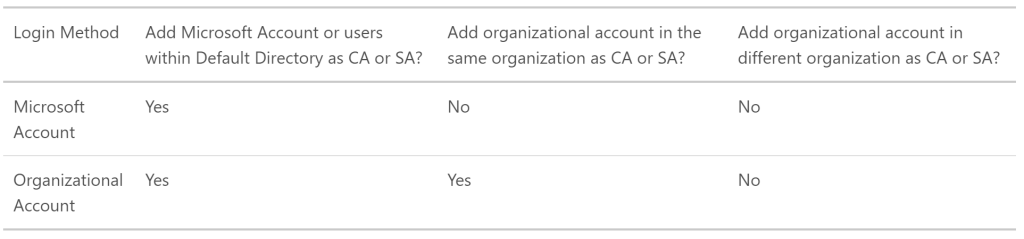
However if you do have the limited Default Directory, you can create a new Azure AD directory under the subscription, then you can change the default directory in which the Azure subscription uses. This will then allow you to add both Work/School and Microsoft Accounts. How? See https://support.microsoft.com/en-au/kb/2969548
There are separate roles for Azure AD as follows, remember these have nothing to do with Azure itself. The following are the different Directory Administrator roles.
- Global Administrator
- Billing Administrator
- Service Administrator
- User Administrator
- Password Administrator
Then there’s Azure itself. With Azure there’s the subscription to Azure itself which is more of a billing thing, this is where Azure based roles come in.
The Azure based roles are slightly different considering what Azure platform you are using, whether ASM(Azure Service Management (Classic)) or ARM (Azure Resource Management).
ASM (Azure Service Management (Classic))
Remember, depending on how you signed up with Azure, you can add both Organisational Accounts to these roles as well as Microsoft Accounts, or just Microsoft Accounts.
- Account Administrator
- Service Administrator
- Co-Administrator
Each subscription has a Service Administrator (SA) who can add, remove, and modify Azure resources in that subscription. The default SA of a new subscription is the AA, but the AA can change the SA in the Azure Accounts Center.
Subscriptions have an association with a directory. The directory defines a set of users. These can be users from the work or school that created the directory or they can be external users e.g. Microsoft Accounts. Subscriptions are accessible by a subset of those directory users who have been assigned as either Service Administrator (SA) or Co-Administrator (CA); the only exception is that, for legacy reasons, Microsoft Accounts (formerly Windows Live ID) can be assigned as SA or CA without being present in the directory.
This diagram takes a step above the Azure Account / Tenant level into the Enterprise EA level just so you can see the overall perspective from the entire hierarchy. However, many of you would be setup with Azure in the middle (account) level by possibly using a credit card or other type of licensing. Or some might be setup with the bottom level only in the case of CSP licensing.
Here’s the reference URLs I got the information from:
How Azure subscriptions are associated with Azure Active Directory
Understanding resource access in Azure
ARM (Azure Resource Management)
How does the above ASM based Classic roles tie in with Azure Resource Manager roles? Remember, Azure AD remains the same with the same Directory Administrator roles, the difference being the different administrator roles on the Azure ARM platform.
The built-in core roles are as follows and have no affiliation or access to ASM:
Owner: Let’s you manage everything, including access to resources
- Closest ASM match: Service Administrator
Contributor: Let’s you manage everything except access to resources
- Closest ASM match: Co-Administrator
Reader: Let’s you view everything, but not make any changes